Wireguard server on Raspberry while being an OpenVPN client
Written by pmd - - no commentsThis is follwoing these first notes written a while ago : Wireguard on Raspberry
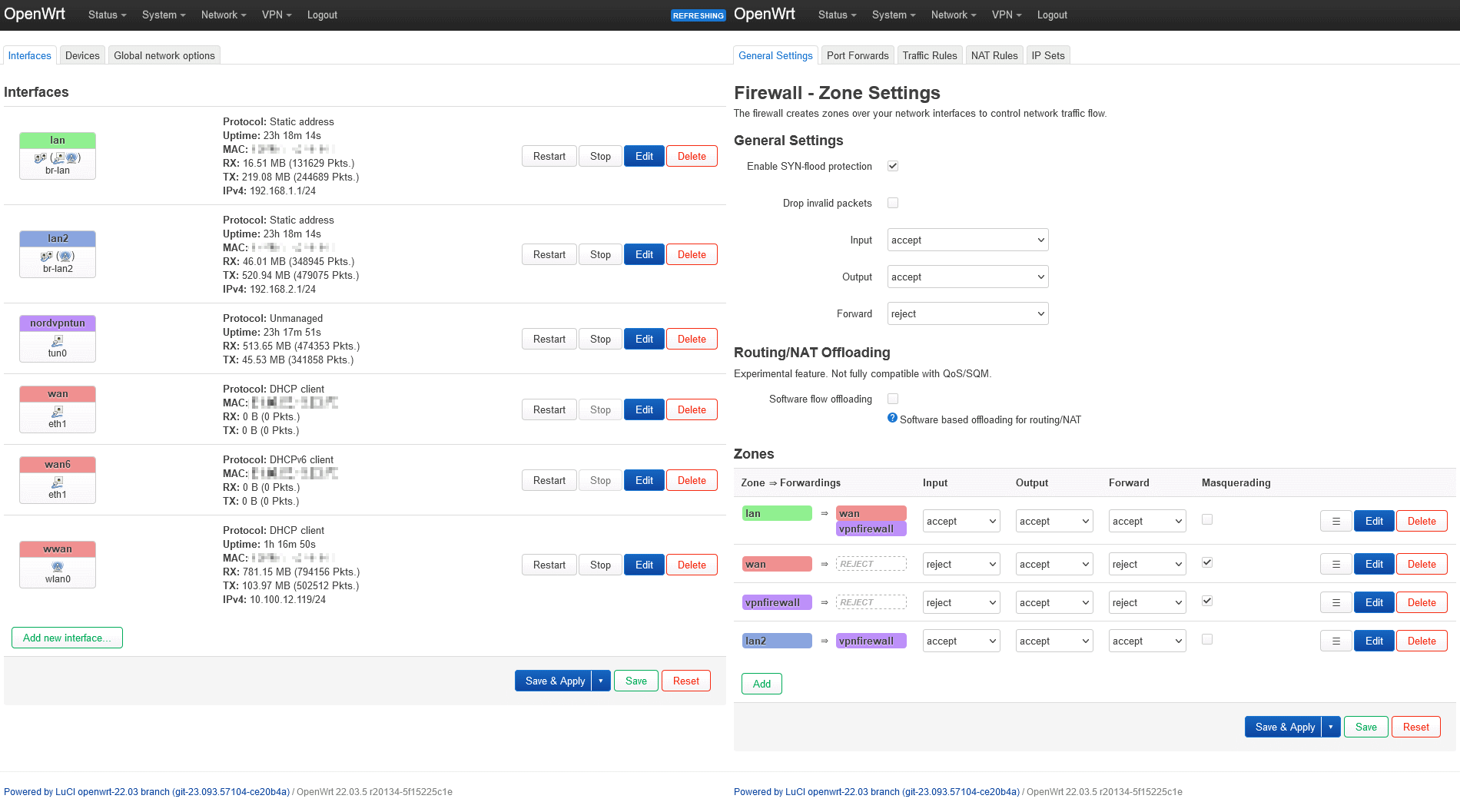
Context
The Raspberry is already an OpenVPN client : see here.
- All packets that are not tagged '42' are using main route table (which outputs to OpenVPN tunnel).
- All packets that are tagged '42' are using route table 42 (which outputs to internet link).
For my use case, all Wireguard packets will need to be routed as specified in table 42.
Wireguard server setup
I used this guide to globally setup wireguard and a few clients (lastest updated using iptables): Installing and Configuring WireGuard on Raspberry Pi OS (September 2021)
The generated configuration was the following:
Server:
[Interface]
Address = 192.168.99.1/24
ListenPort = 58280
PrivateKey = gNVxJe7Se842IiOR5GsXeM4sHcacGhPATIdQCgqP8Wa=
PostUp = iptables -A FORWARD -i %i -j ACCEPT; iptables -A FORWARD -o %i -j ACCEPT; iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
PostDown = iptables -D FORWARD -i %i -j ACCEPT; iptables -D FORWARD -o %i -j ACCEPT; iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
[Peer]
PublicKey = OQmmvh9/8PDWFIpOEzVWzOZ1HXQ48+10vONFlUNb0ia=
AllowedIPs = 192.168.99.2/32
Peer 1:
[Interface]
Address = 192.168.99.2/24
PrivateKey = 6OfJPX1ZQCFu08fTy2uU6JdgUf/qXgzBoTtX/tCYX3a=
[Peer]
PublicKey = b6kqDH4pjAdK0LqPrEF4Fc9d4XxR0Eb3kSk9rzdEKma=
AllowedIPs = 192.168.99.1/32, 192.168.1.0/24
Endpoint = adress.ddns.net:58280
Adding other users
⚠️ ⚠️ ⚠️ Be sure to make a copy of your wireguard configuration because it will be overwritten.
$ sudo wg-quick up wg0 # make sure Wireguard is running
$ sudo ./wg_config/user.sh -a another_user # creating new user
$ ls ./wg_config/users/another_user/ # look at all files generated
total 32K
drwxr-xr-x 2 root root 4.0K Sep 21 15:56 .
drwxr-xr-x 6 root root 4.0K Oct 9 18:16 ..
-rw-r--r-- 1 root root 216 Sep 21 15:56 client.all.conf
-rw-r--r-- 1 root root 238 Sep 21 15:56 client.conf
-rw-r--r-- 1 root root 900 Sep 21 15:56 another_user.all.png
-rw-r--r-- 1 root root 1016 Sep 21 15:56 another_user.png
-rw-r--r-- 1 root root 45 Sep 21 15:56 privatekey
-rw-r--r-- 1 root root 45 Sep 21 15:56 publickey
$
IP forwarding
For clients to be able to join each other and access internet, it is necessary to enable IP forwarding:
net.ipv4.ip_forward = 0
$ sudo sysctl -w 'net.ipv4.ip_forward=1'
net.ipv4.ip_forward = 1
$ sysctl net.ipv4.ip_forward
net.ipv4.ip_forward = 1
Adjustment
Because of the context described above it wasn't enough to have a working link.
I had to add few lines for it to work on server and client sides. See below:
Server:
[Interface]
Address = 192.168.99.1/24
ListenPort = 58280
PrivateKey = gNVxJe7Se842IiOR5GsXeM4sHcacGhPATIdQCgqP8Wa=
FwMark = 0x2A # if packet not tagged '42' it will be routed to tun0 interface
PostUp = iptables -A FORWARD -i %i -j ACCEPT; iptables -A FORWARD -o %i -j ACCEPT; iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
PostUp = ip route add 192.168.99.0/24 dev wg0 proto kernel scope link src 192.168.99.1 table 42 # route table update for packet tagged '42'
PostUp = sysctl -w 'net.ipv4.ip_forward=1' # activate IP forwarding
PostUp = ip rule add from 192.168.99.0/24 table 42; ip rule add to 192.168.99.0/24 table 42 # all packet comming/leaving from 192.168.99.0/24 should use table 42
PostDown = iptables -D FORWARD -i %i -j ACCEPT; iptables -D FORWARD -o %i -j ACCEPT; iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
PostDown = sysctl -w 'net.ipv4.ip_forward=0' # disactivate IP forwarding
PostDown = ip rule del from 192.168.99.0/24 table 42; ip rule del to 192.168.99.0/24 table 42
[Peer]
PublicKey = OQmmvh9/8PDWFIpOEzVWzOZ1HXQ48+10vONFlUNb0ia=
AllowedIPs = 192.168.99.2/32
Peer 1:
[Interface]
Address = 192.168.99.2/24
PrivateKey = 6OfJPX1ZQCFu08fTy2uU6JdgUf/qXgzBoTtX/tCYX3a=
DNS = 208.67.222.222, 208.67.220.220
[Peer]
PublicKey = b6kqDH4pjAdK0LqPrEF4Fc9d4XxR0Eb3kSk9rzdEKma=
AllowedIPs = 0.0.0.0/0
Endpoint = adress.ddns.net:58280
Start, monitor and stop wireguard
[#] ip link add wg0 type wireguard
[#] wg setconf wg0 /dev/fd/63
[#] ip -4 address add 192.168.99.1/24 dev wg0
[#] ip link set mtu 1420 up dev wg0
[#] iptables -A FORWARD -i wg0 -j ACCEPT; iptables -A FORWARD -o wg0 -j ACCEPT; iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
[#] ip route add 192.168.99.0/24 dev wg0 proto kernel scope link src 192.168.99.1 table 42
[#] sysctl -w 'net.ipv4.ip_forward=1'
net.ipv4.ip_forward = 1
[#] ip rule add from 192.168.99.0/24 table 42; ip rule add to 192.168.99.0/24 table 42
$
$ sudo wg
interface: wg0
public key: b6kqDH4pjAdK0LqPrEF4Fc9d4XxR0Eb3kSk9rzdEKma=
private key: (hidden)
listening port: 58280
fwmark: 0x2a
peer: OQmmvh9/8PDWFIpOEzVWzOZ1HXQ48+10vONFlUNb0ia=
endpoint: 96.82.73.111:32378
allowed ips: 192.168.99.2/32
latest handshake: 37 seconds ago
transfer: 425.32 KiB received, 502.92 KiB sent
$
$ sudo wg-quick down wg0
[#] ip link delete dev wg0
[#] iptables -D FORWARD -i wg0 -j ACCEPT; iptables -D FORWARD -o wg0 -j ACCEPT; iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
[#] sysctl -w 'net.ipv4.ip_forward=0'
net.ipv4.ip_forward = 0
[#] ip rule del from 192.168.99.0/24 table 42; ip rule del to 192.168.99.0/24 table 42
$
Enabling at startup
Once everything is working you can enable Wireguard at startup by doing: